This document provides a comprehensive overview of the email flow process, detailing how an email travels from the sender to the receiver’s inbox. It outlines the critical steps involved, including the use of SMTP, MX records, and the verification of SPF, DKIM, and DMARC. Additionally, it discusses the various anti-spam and anti-virus measures that emails must pass through to ensure successful delivery.
Email Flow Process
-
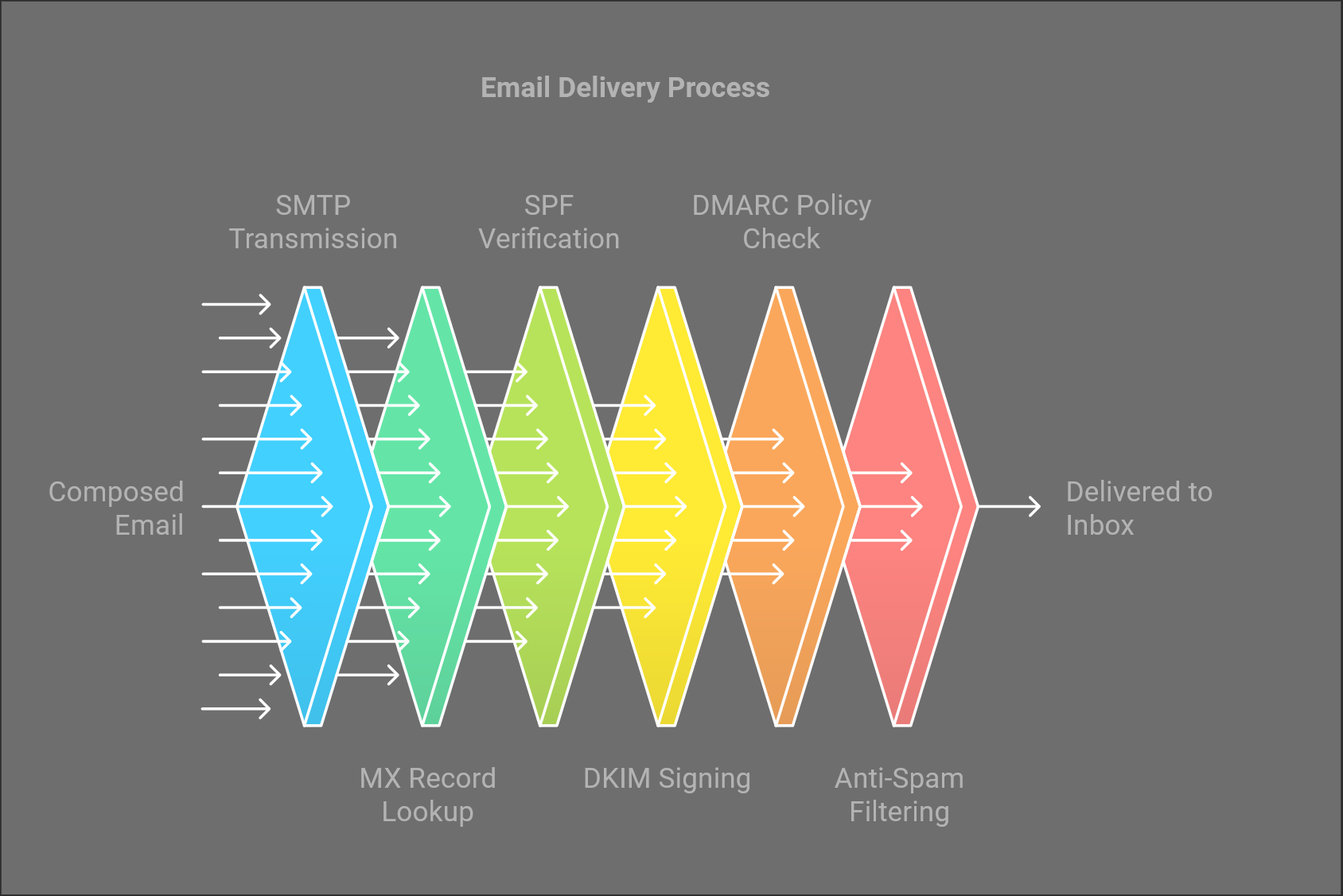
Sender Initiates Email: The process begins when a sender composes an email and hits the send button.
-
SMTP Protocol: The email is transmitted using the Simple Mail Transfer Protocol (SMTP). This protocol is responsible for sending the email from the sender’s mail server to the recipient’s mail server.
-
Finding MX Records: The sender’s mail server queries the Domain Name System (DNS) to find the Mail Exchange (MX) records associated with the recipient’s domain. MX records specify the mail servers responsible for receiving emails on behalf of the domain.
-
Email Acceptance: Once the sender’s server locates the appropriate MX record, it attempts to deliver the email to the recipient’s mail server.
-
SPF Verification: The recipient’s mail server checks the Sender Policy Framework (SPF) record to verify that the sender’s IP address is authorized to send emails on behalf of the sender’s domain. If the SPF check fails, the email may be rejected or marked as spam.
-
DKIM Signing: The email is checked for DomainKeys Identified Mail (DKIM) signatures. DKIM adds a digital signature to the email header, allowing the recipient’s server to verify that the email has not been altered in transit and that it is indeed from the claimed sender.
-
DMARC Policy: The recipient’s server then checks the Domain-based Message Authentication, Reporting & Conformance (DMARC) policy. DMARC builds on SPF and DKIM, providing instructions on how to handle emails that fail authentication checks.
-
Anti-Spam Filters: After passing SPF, DKIM, and DMARC checks, the email is subjected to various anti-spam filters. These filters use algorithms, including Bayesian filtering, to assess the likelihood of the email being spam based on its content and sender reputation.
-
Anti-Virus Scanning: The email is scanned for viruses and malware. This step is crucial for protecting the recipient’s system from potential threats.
-
Compliance with Rules: The email must comply with a series of predefined rules set by the recipient’s mail server. These rules may include checks for blacklisted IP addresses, content filtering, and attachment policies.
-
Delivery to Inbox: If the email successfully passes all the above checks, it is finally delivered to the recipient’s inbox. If it fails any of the checks, it may be redirected to the spam folder or rejected altogether.

Recent Comments